Category: Technology
By the late 1980’s the prominent sound of “ding, ding, zip” of the typewriters that reverbed through the office halls gave way for a softer, mimicked, mechanical feel of the typewriters. The computer keyboards with time evolved, making it the familiar yet a distinct avatar of the faithful typewriters of the past. What changed was more than just the mechanical clinker in the office halls; they gave rise to a new status quo on how work was performed and what could be achieved by ideally leveraging the computers.
A Digital Revolution
A little bit of reflection on the successful business of our times like Facebook, WhatsApp, Zynga, Twitter, Square, Netflix, points to the fact that, these companies were either born digital or made efforts to alter their business to becoming digital. The companies that innovated, the ones that laid the old to rest, followed a process of creative destruction. What businesses have to remember is that, most of the times the employees and the customers have got a faster affinity to adapt to changing technology. This adoption would only be followed by an expectation that the business that they interact with, also follows suit. For B2B players it becomes important that they use Mobile, Big Data, IoT, 5G, and augmented reality for revolutionising the customer experience, optimising operational and industrial processes, innovating rapidly, bringing faster cash cycles, driving employee productivity and for improved service enhancements.
Statistics shows that there would be 6.1 billion smartphone users worldwide, 56% of all web traffic is through mobile and the global mobile data traffic is expected to reach 6.2 Exabytes/ month! That’s a lot of numbers indicating the importance of a Mobile strategy.
Digital Business Transformation through Mobility
Mobility is not just about going wireless. It focuses on the business process and the work models that effectively utilise mobile. Internally it is about the business models and processes that can enable marketing, HR and operations to utilise the benefits of going mobile like improved and faster decision making, increased productivity of the employees, faster resolution of internal issues, brand perception enhancements, reduced sales cycle time and increased revenues. But there are concerns of network security, compatibility and security of the devices, corporate and customer data security, regulatory requirements that always make the C-Suite executives think twice before they tread on these unsure waters.
Transforming a business through mobility has to have a well-rounded view of the entire business and a thorough recognition of the priorities of going mobile. It can be as simple as supporting more mobile handheld devices, extending internal systems for mobile access, offering incremental BYOD, providing more mobile support to the customer, implementing corporate mobility policies and so on. With Mobility, work becomes something that people do and not a place they go to, it has the capability to bring transformations with regards to:
Increased Revenue Potential
Mobility is pervasive and the ever trusted smartphone has led the march, becoming the go-to device, people use for work, pleasure or to kill boredom. Living in the comfort of your pockets, the mobile becomes the first medium of choice for one to interact with the outside world. This gives business a chance to connect to the customers at any point of time. Similarly, mobile apps that can help the customer consume products and services would invariably help to increase revenues. Employee empowerment and customer engagement are the two critical interactions for a business to make. Having a solid mobile strategy would help them both to be connected on the move, thus effectively enabling contracts and deals closures on real-time.

Flexibility
The first signs of going digital would be improved employee freedom. An employee would no longer be restricted to the cubicles, instead he/she will get a chance to work on ‘wherever whenever’ style. Through cloud-based applications, the staff would be able to access resources and attend to important work, no matter where they are. Such apps are now even built with offline connectivity that can help the field workers to sync things later into the cloud while effectively helping them perform their work. Reach out is one such app that has been developed with the offline connectivity, for managing work orders and jobs in inspection and audits. This goes a long way into providing flexibility, responsiveness and faster turnaround times, which in the end translate to excellent customer satisfaction. This sets up a win-win for both the customer and the business as it enhances the way you work and the way the business serves the customers need.
Collaboration
Another major contributor to employee productivity is the way mobility enables workplace collaboration, regardless of the physical proximity of individuals and teams. When effective collaboration is required among individuals and teams spread across multiple locations, mobile truly makes the effort more streamlined and natural. Cloud-based enterprise collaboration software can help teams to break down barriers of location and time, bringing the best of talents to work in unison.

Communication
With the flexible and collaborative nature of work, there comes a need of precise and timely communication that can draw the line between being successful or crashing out. It becomes highly essential that the mobile workforce is appraised with relevant metrics that help them to take the right decision and also to update crucial project updates. Aware mobility helps to accelerate performance by having this view of important metrics right on your trusted iOS or Android device. This can help to get on time information that helps you take that important decision when required.
Operational Efficiency and Productivity

Businesses would have to change the way they have conducted themselves over the years. They would need to get re-organised, to accommodate the task oriented usage style of mobile users and deliver them efficiently, without having any security concerns. Real time statistics of location and direction have already helped logistics and field service, to come up with strategic ways in which these could be leveraged. This leveraging should ideally result from a re-envisioned business process. Mobilisation of Salesforce interactions, supply chain management and innovative charging models can be devised by having mobile at the hub of the transformation, for a truly digital organization.
Stay up to date on what's new

Featured Blogs
Stay up to date on
what's new



Talk To Our Experts
Business leaders, often focusing on the immediate and the more pressing, relegate internal processes to the secondary. As a result, inefficiencies of various hues creep in, over time.
Inefficiencies manifest in many ways. Business processes and systems may be aligned to suit the technology rather than technology being applied to conduct business in the most seamless way. Additional processes may have come up to complete a part of the original process. Often, critical gaps in business processes and data silos make employees struggle to find the right information, or the right tools. The Boston Consulting Group estimates the amount of “procedures, vertical layers, interface structures, coordination bodies, and decision approvals” having increased by anywhere from 50 percent to 350 percent over the last fifteen years, in US and European companies, with managers spending as much as 40% of their time writing reports, and 30% to 60% of their time coordination meetings! The net result is invariably business executives having to work harder than necessary.
One knee-jerk reaction when such inefficiencies become too disruptive to be ignored is automation. However, mere automation of inefficient processes only accentuates waste. While automation is indeed a step in the right direction, businesses need to also make their processes smarter.
Here are a few ways in which business processes can be tweaked to enable working smart instead of working hard.
- Standardize processes, but one size does not always fit all. What works well in one division may not work well for the company overall. 3M found this out the hard way when they applied Six Sigma not just in accounting, but across-the-board, resulting in stifled innovation in a company where innovation is the key USP.
- Innovate. A 2011 PwC study reports 80% of CEOs believing innovation to drive efficiencies and providing a competitive advantage.
- Leverage on-demand and scalable cloud solutions such as PaaS and IaaS to optimize resources, reduce costs, create innovative products and services, and add value to existing business systems.
- Apply technology to tighten collaboration between stakeholders, including customers. Celina Insurance Group implemented a highly collaborative extranet to bring the company employees, 500+ independent agents and customers closer, and offer easy access to all relevant information, resulted in massive gains.
- Integrate the supply chain with business processes, across the value-chain, in real time, to connect people with the information they require. Diary major Danone reduced the timeline of its production optimization plans from two days to a mere 15 minutes now, by updating and integrating its production planning and scheduling technology.
- Leverage analytics to get a 360-degree view, and derive value, from available data. Apply emerging technologies to unlock data and information resident in physical and digital systems, and subject such data to analytics. Ensure such new intelligence is readily available to those in a position to use it, and actionable to make better decisions.
- Enable a mobile workforce capable of collaborating anytime from anywhere. Today’s executives and customers are always on the move. Mobile apps and workflows save time, improve efficiency, and also unlock new possibilities.
About 70% of CEOs invest in IT to reduce costs and to become more efficient, and 54% of them focus on growth initiatives powered by emerging technologies such as mobility. About 80% of manufacturing businesses expect mobile apps to increase their productivity by at least six percent. Mobile phones powered by cloud-based storage and apps allow employees to save a whopping 57 minutes a day, on average.

Smart employees are already up to the task. They often cobble up their own solutions, taking advantage of the tons of resources available online, when existing business resources do not meet their requirements. About 90% of all employees use cloud-based services, such as Skype and LinkedIn, for their work, and 79% of employees use cloud-based file sharing and collaboration tools, such as Dropbox or Microsoft OneDrive. Needless to say, such improvisations do not do away with all inefficiencies and come with grave security and data privacy risks.
Businesses need to facilitate smart employees by developing custom apps that automate workflows, provide digital forms, and sync offline data. A major stumbling block is the extensive time and resources that development of new custom apps requires. IT departments, already hard-pressed to keep existing systems running, often find the task of designing and updating apps that need to work with multiple platforms and disparate devices, too onerous. The solution is to partner with experienced providers, who not only make available complete and customized solutions, but also chips in with their specialized expertise and experience, to realise smart business processes.
Partnering with us allows you to have the best of both worlds – ability to roll out apps that leverage the latest cutting edge technology to enable smart business processes, without straddling your already overburdened and resource-crunched IT team with more responsibilities.
Stay up to date on what's new

Featured Blogs
Stay up to date on
what's new



Talk To Our Experts
Steve Jobs’s April 2010 prophecy of mobile devices replacing desktops and laptops as the computing devices of choice is now coming true. More people now access the internet using their mobile devices, compared to desktops or laptops. This has its effect in e-commerce as well.
M-commerce is now 34% of all ecommerce transactions, and expected to grow at 31% in 2017. Overall e-commerce is slated to grow at just 15% in the same period, meaning m-commerce is slated to grow 200% faster. Goldman Sachs estimates the total value of m-commerce at $626 billion by 2018, by which time m-commerce would account for half of all e-commerce transactions.
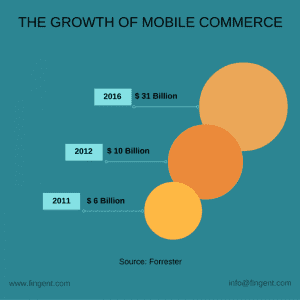
The reason for the surge in m-commerce is obvious. More and more people now prefer the convenience of taking out their smartphones when on the move in a commuter train or when whiling away time at the dentist’s office, rather than take time out to sit in front of a desk, wait for the laptop to boot, and get connected.
Many e-commerce players, quick to spot the trends, have come up with responsive mobile websites and rolled out native mobile apps, to facilitate the mobile-savvy customer. In fact e-tailers no longer have a choice; as 57% of customers won’t even recommend businesses with poor mobile sites, leave alone patronize it. However, most of the early adopters have also discovered merely launching mobile apps or mobile websites is not enough. It is still a fiercely competitive marketplace, and only those who go all out to facilitate the mobile customer wins.
Here are some ways to go all-out, to pamper the highly fickle mobile shopper
Leverage the Power of Simplicity.
The mobile is a consumption-focused device. Play to this strength by making it easy for the user to find what they are looking to consume. Leverage the power of simplicity through a minimalist design and a clean structure. The best apps do not require too much keyboarding or taping on menus, and makes all crucial process, be it registration, login, ordering, check-out, and payment fast and easy. Simplicity and minimalism offers a residual benefit of minimizing data traffic, and speeding up page-loads, which in turns boosts SEO.

Think like a Mobile Customer
The path and trajectory of desktop and mobile user are diametrically different. Successful e-tailers understand the customer’s journey and design the mobile experience around it, delivering a good UX. For instance, since most mobile users shop when on the move, or in the midst of doing something else, anything that shortens interaction time boosts the chances of conversion. Also, since mobile users generally prefer browsing different products, and as such, navigate different screens before actually making a purchase, making it easy to browse many products, add items to the cart, and check out later increases the chances of conversion and making long-term fans. Successful e-tailers also leverage analytics to personalize for the customer, taking into consideration the extremely personal nature of mobile devices.
The path and trajectory of desktop and mobile user are diametrically different. Successful e-tailers understand the customer’s journey and design the mobile experience around it, delivering a good UX. For instance, since most mobile users shop when on the move, or in the midst of doing something else, anything that shortens interaction time boosts the chances of conversion. Also, since mobile users generally prefer browsing different products, and as such, navigate different screens before actually making a purchase, making it easy to browse many products, add items to the cart, and check out later increases the chances of conversion and making long-term fans. Successful e-tailers also leverage analytics to personalize for the customer, taking into consideration the extremely personal nature of mobile devices.
The path and trajectory of desktop and mobile user are diametrically different. Successful e-tailers understand the customer’s journey and design the mobile experience around it, delivering a good UX. For instance, since most mobile users shop when on the move, or in the midst of doing something else, anything that shortens interaction time boosts the chances of conversion. Also, since mobile users generally prefer browsing different products, and as such, navigate different screens before actually making a purchase, making it easy to browse many products, add items to the cart, and check out later increases the chances of conversion and making long-term fans. Successful e-tailers also leverage analytics to personalize for the customer, taking into consideration the extremely personal nature of mobile devices.

Leverage the Power of Innovation
The overriding focus of successful e-tailers is how to uniquely serve their mobile customers. They strive to make their mobile assets dynamic, through promos, deals, offers, discounts, and more. In this, they innovate to ensure their apps leverage the latest developments in technology, or to ride the latest smartphone trends. The best m-commerce apps leverage the unique capability of mobile devices, such as geo-targeting, location-based services, QR codes, and more, to deliver customized offers and deals, and other value-added services.

Integrate Mobile with Overall e-Commerce Strategy
A mobile friendly website or a native app may induce the customer to make a purchase immediately. However, for all the efforts put in by the e-tailer, there is always a possibility of sheer hardware limitations driving poor mobile experience. As such, it is important to integrate the mobile strategy with the overall e-commerce strategy, and provide a consistent experience across channels, where a customer may “capture” of the purchase on mobile and complete the transaction on a larger screen. This is even more important as 53% of customers look at products in brick and mortar store and buy online.

Tie in m-Commerce with Social Media
Mobile and social media are almost inseparable. Facebook, Twitter, Snapchat, Instagram, and the likes are on the screens of nearly everyone stuck on the subway, bus, or train. Successful e-tailers who integrate their m-commerce strategy with their social efforts are able to draw in quite a number of social media visitors straight to the m-commerce site.

There is however, no one-size-fits-all solution. The best way to milk the ongoing m-commerce revolution depends on your specific business. Partnering with us to expand and enhance your mobile strategy allows you to leverage our wide experience and expertise, and is a guaranteed way to save time and improve your ROI.
Stay up to date on what's new

Featured Blogs
Stay up to date on
what's new



Talk To Our Experts
There are components in business that ride the wave of time to have halo’s associated with it, when space, time and the event coincide, the companies that wear the halo accelerates its reach and hits the bull’s-eye. The resulting amalgamation of people, processes and ideas have time and time again celebrated success. This has been etched in stone, but what’s more contrasting and less surprising is that the components that create the halo is never the same and are subjected to disruption from around. There were innovations that elevated organizations and disruptions that have catapulted few others to the top. Particularly, the digital forces that once was touted as a disruption, which is now increasingly becoming the norm for the future.
The Whole Picture
Digital Transformation is not about islands of digitization like digital marketing, digital customer behavior or transformation from paper to digital media within an organization, rather it is a demanding process that requires considerable time, holistic thought and skilled people to guide the transformation process. The change has to be ideally driven from top-down, where the business leaders can put together the pieces of the digital puzzle thus enabling a rapid transformation in the business processes, activities and work models to move faster and efficiently to meet customer and business needs. This transformation of business by leveraging technology ultimately rests on the people who can drive the change into all layers of the organization.
Common Frontiers, Different Approach
Digital as the way forward is being experimented at varying degrees and varying pace by organizations. Some become more successful than the other to make this change a holistic one that touches the entire organization. The successful organizations show traits of digital maturity that touch different areas within an enterprise like Marketing, Operations, HR and Customer service; business models that unite these areas, and processes that embed efficiency through business automation, optimization, and management.
The foundation of successful transformation into the digital realm lies in organizational change, this change needs to address some key areas:
- For existing business, there is a need to take stock and understand why to transform, what to transform and how to transform. Once the reflection is carried out and you have figured out the answers to these questions, you should ideally start your mission to a digitally modified business. Improving on digital lines can help to have improved decision making by the use of big data, analytics, creating an effective corporate control, Risk optimization by automating manual labor, improved targeting with insights from customers, augmentation of traditional channels into digital and whenever wherever service propositions as well. Granted your journey would require much change from the status quo, and even you may not be as digital as a “Born Digital” company, but effective action can leverage the existing business, giving better reach to help multinational companies to truly have global operations.
- For an organization, Digital transformation process is multifaceted. Right from the beginning, it is essential that the organization has leaders with the potential to drive this change. The company has to make changes in their best practices in business architecture, BPM, continuous improvement, continuous innovation, crowd computing etc. Latest tools for robotics and sensors that can automate much of the mundane, so that the organization can focus on building lasting relationships with the customer. A mix of digital technologies, tools, and best practices can set the stage for Digital Transformation.
- The end part of the digital transformation is the customer experience. The models, the processes and the coherence of the activities carried out within an organization should ideally drive the customer journey with an emphasis on the physical and digital touch points. With Digital it is possible to effectively map this journey by understanding the way the customer interacts with business and brands, this invariably helps to find the best-fit solution for the customers. This is made possible through the combination of software, IoT, Big data, Mobile, CRM, Augments reality etc. In reality, a company may not be able to perform all these alone, it would have to seek partners that can run part of the show for them so that the companies can, in turn, focus on building their main offering.
The final touch points, like the interface, should invariably help the customer feel at ease and add touches of modernity. Looks aren’t everything, but when you and your competitor have the same product, looks, and a streamlined interface would come in handy
The Digital Wave doesn’t mean to throw away the method in which the business is being currently being conducted, rather it should dovetail and leverage the current best practices. When this is executed in the right way, the businesses can cater to a wider array of customers, speed to hit break even in shorter time, improve workflow employee efficiency within the organization. All companies irrespective of the segments they cater must invest proportionally so that risks can be mitigated and key opportunities are addressed in the most prudent way.
Stay up to date on what's new

Featured Blogs
Stay up to date on
what's new



Talk To Our Experts
In today’s hyper-connected age, with people always on the move, one would think not developing enterprises mobility solution is akin to the company shooting itself on the foot. Yet many companies hesitate to develop mobility solutions, wary as they are about misconceptions associated with it.
Here are the top six myths related to enterprise mobility solutions.
Myth # 1: Legacy Software is Too Entrenched to Displace
Legacy software is often the whipping boy for enterprises who refrain from developing mobility solutions. A key accusation is legacy software draining IT budgets, making it hard to fund new software.
The reality is that developing new mobility software doesn’t require massive investment. In fact, today’s rapidly advancing mobile solution landscape makes it possible to develop mobility solutions with little or no programming skills, with a fraction of the cost, time, and effort it takes to develop traditional solutions.
The problem comes when many enterprises try to throw in more servers as the solution to every IT problem they confront. Smart enterprises simply leverage scalable and affordable cloud-based solutions, which does not involve CAPEX costs.
Moreover, investment in mobility solutions often pays back for itself quickly, as mobility allows the company to become lean and mean, and spare the costs required to maintain legacy systems.
Myth #2: Enterprise Silos Make Mobility Solutions a Non-Starter
Most organizations that have been around for a while live with data and software silos. Sales, HR, Marketing, Finance, and other teams all use different tools, and operate disparate enterprise systems.
While data silos are indeed a drag and removing it can be game-changers for enterprise transformation, silos needn’t necessarily come in the way of developing mobility solutions. Installing a remote desktop server on the legacy system makes it easy to access data on it. If the legacy system doesn’t allow remote access, it is obsolete anyway. Also, many mobility apps can actually live with silos, and when information is required cutting across silos, there are several cost-effective analytic solutions now available that can access data from different silos and collate it in the cloud.
Myth#3: Potential Disruptions Create More Havoc than the Gains Mobility Brings
Many companies are inspired by the famous adage “if it ain’t broke, don’t fix it,” and refuse to dabble with mobility solution, least the upgrade disrupts what is already working. They consider the difficulty of migrating legacy business software and data, the downtime it causes to business critical processes, and the possible need to overhaul data center hardware and software. While such challenges were indeed big stumbling blocks in the past, the advancement of software-as-a-service (SaaS) solutions solve much of these issues. SaaS upgrades are in most cases done overnight, and does not require investment in new hardware or software.
Myth#4: Password Overload and Other Ills Breed End-User Resentment
No enterprise initiative succeeds with the support and cooperation of end-users. While enterprise mobility help end-user employees in many ways, they often raise concern about having to remember many passwords for the various enterprise apps they need to access. They forget passwords and raise tickets, dragging IT resources for account recovery.
While the concern is genuine, easy solutions are also available, most notably in the form of unified, easy single sign-on (SSO). Using SSO, a user needs to login just once, to gain access to all systems. SSO even facilitates integration with the user’s Google Account, or the credentials used to access Microsoft Office 365.
Myth #5: Inadequate Training and Support Doom Implementation
A common grouse against new solutions in general and mobility solutions in particular, is employees not getting enough training on enterprise apps to be productive.
The problem is actually misplaced, and has to do more with the design of the mobility solution than lack of training. Mobile apps are primarily meant to be easy, explicit, and self-evident. A “kitchen sink” (all-encompassing solution) mobile app, replicating the features and functionality of desktop applications rarely succeeds as it just combines the worst of both worlds. The ideal enterprise mobile apps rather contain just a few key functions, focusing on a specific process, and come with limited navigational choices and simple UX, primed for quick access.
Lopez Research Enterprise Mobility Benchmark estimate 60% of companies allowing BYOD, meaning employees would be familiar with device in the first place.
Myth #6: Enterprise Mobility Solutions are a Security Nightmare.
About one in every three companies had their sensitive data compromised through lost or stolen devices. To counter such damning statistics, most enterprises take inspiration from the adage “If you are not there to be hit, you cannot be hit,” and limit mobile access.
Security risks associated with mobility software are real, but also blown out of proportion. A big majority of the victims are either careless, or the company had weak security standards in the first place. Making risk management a key focus within the overall mobility strategy, and deploying effective mobile device management protocols, in combination with advanced encryption, modern authentication mechanisms, and even analytics mitigate most risks, and make mobility solution as safe as on-premises software.
Enterprises are waking up to the need to embarking on a sound mobility strategy, dispelling the myths associated with mobility. Lopez Research Enterprise Mobility Benchmark reveals 68% of companies ranking mobile-enabling the business as a top concern for 2015, a concern surpassed only by securing corporate data, and more than half of the companies planning to build 10 or more enterprise mobile apps in 2016.
Get in touch with us to fine tune your mobile strategy and develop state of the art mobile apps. Our cutting-edge enterprise mobility solutions not just enable your workforce to access much needed critical information anytime and anywhere, but also increase productivity and efficiency, and help you streamline your processes towards facilitating the customer.
Stay up to date on what's new

Featured Blogs
Stay up to date on
what's new



Talk To Our Experts
That the cloud is the backbone of this IoT revolution goes without saying. Reports from the January 2016 Consumer Electronics Show (CES) reveal most manufacturers equipping their devices, be it refrigerators, cars, dishwashers, running shoes, thermostats, and every other conceivable device massive cloud-based back end, to enable such devices to join the IoT bandwagon. The investment in cloud capabilities comes from the twin need to enable these devices to become “smart” by receiving and transmitting data, and to give these devices long-term value by making them instantly upgradable. The cloud facilitates both these IoT objectives.
For IoT to work, the connected device needs to communicate with other “things” and also with whoever holds the control strings. The “thing” connects with cloud servers to receive and transmit data, and store instructions and commands. At another pane, the “small” data from each connected yet disparate “thing” accumulate and become big data in the cloud. The convergence of huge quantities of critical data in a common cloud pane, accessible anytime and anywhere, enables real-time analytics.
The possibilities of such cloud powered real-time analytics to make life better, and for businesses to unlock new opportunities are endless. A few cases in point:
- Traffic controllers can source in small data from hundreds of IoT-enabled traffic signals, and subject it to real time big data analytics in the cloud, to ensure synchronized operation of traffic lights, and deliver seamless movement of traffic.
- Smart sensors attached to a pair of running shoes may clock the runner’s pace and notify them when it is time to replace the shoes. Small data from millions of such shoes would allow shoe manufacturers to predict demand accurately, and target prospects with precision.
- IoT-powered refrigerators can let the homeowner know when food products are reaching their expiration date, or when the stock is running out. It may also transmit data to the supermarket, who can then predict demand accurately, and get their inventory right. In fact, the refrigerator may send off a replenishment order to the supermarket automatically.
Millions of sensors embedded on things already monitor and track data of all hues, and deeper insights from the analysis of such big data facilitate better-informed decisions and responses, cutting across industries and sectors.
But is the cloud really necessary for all this? Can IoT make itself useful without the cloud?
The IoT ecosystem that enables the possibilities would not be possible without back-end cloud-based applications that churn, translate and transmit valuable intelligence.

With terabytes of data flowing in from millions of disparate connected “things,” the cloud is the only viable platform that can filter, store, and enable access of the required information, in useful ways.
The amount of incoming data from connected devices sensors often fluctuates widely. A sensor may generate 1000 KB of data in a day, 4TB on another day, and may not generate any data at all on a Sunday. The elasticity of the cloud enables scaling up or scaling down resources to absorb such wide fluctuations of data.
Hybrid cloud systems facilitate IoT-enabled services to communicate with geographically distributed back-end systems. This anytime anywhere connectivity is indispensable for real-time analytics, and to enable path-breaking business models and public services.
The cloud back-end does away with the near-impossible alternative of regularly updating thousands of individual “things.” Updates are a part and parcel of any system’s life, and is unlikely to go away anytime soon.
The built-in security of the cloud assures that data is protected and compliance standards are baked into the platform.
For all the enablers of the cloud, security remained a drawback. For instance, IoT enabled driverless cars, with cloud servers providing navigation instructions to car, but what if someone hacked into the public cloud server and send the passengers to Kingdom Come! Newer purpose-built clouds that device developers may share or use exclusively offers viable solutions to such security risks, combined with newer tools that protect from information leakage and iron out the few remaining chinks in the cloud armor.
The cloud and IoT being an inseparable couple cuts both ways. Even as the IoT requires the cloud to work, the cloud is evolving to better serve IoT. In fact, IoT is now a chief focus of the cloud.
As the number of connected devices increases exponentially, cloud infrastructure is on the threshold of a massive scale up, to accommodate the data swell. Unique, custom build hybrid cloud deployment models, leveraging the latest advances in software and networking, designed to meet the needs of customers’ unique workloads, enable IoT players to maximize the potential the cloud offers, without being hassled by availability, performance and security issues. Side by side specialized cloud-based service software, systems and skill development is in a boom phase, as is bandwidth improvements to facilitate transmission of data between “things” and the cloud.
A case in point, Microsoft’s recently launched Azure Functions, a “server-less compute,” allowing developers to create apps that automatically respond to events is one such path-breaking service launched recently. Microsoft’s Azure Service Fabric platform-as-a-service (PaaS) platform makes it possible to decompose applications into microservices, for increased availability and scalability.
The IoT revolution is well underway, but as things stand, only the tip of the IoT iceberg has been touched, with just 0.06% of things that could be potentially connected to the Internet being currently connected. However, growth is exponential, with 328 million new “things” being connected to the IoT ecosystem every month. The cloud infrastructure is gearing up simultaneously, to enable a whole new world of cloud powered IoT.
Fingent delivers technologies to enable your IoT solutions— cloud, networks and gateways, heterogeneous device support, systems capabilities, and data analytics. We provide industry-specific solutions that improve productivity and operational efficiency, with exceptional reliability and security. Learn about Fingent’s IoT System
Stay up to date on what's new

Featured Blogs
Stay up to date on
what's new



Talk To Our Experts
Work related injuries account for about $250 million in the United States, across several industries. And out of this, about 20% of them have been found to be lower back injuries. As a matter of fact, according to the U.S Bureau of Labor Statistics, back injuries accounted for a major number of lost employee work days.
Most organizations do know the importance of occupational health and safety practices, yet a lot of them still struggle to maintain it. Even though there are a number of systems available for it, organizations find it hard to decide the effectiveness of one over the other.
This is Where Wearable or Wearable Technology can Help.
Injuries can happen by chance, and sometimes they are unavoidable, like an accidental slip, or fall. Most other times though, one of the major causes of injuries is a lack of proper technique in performing a job. For instance, in the case of loading and unloading, often asymmetrical loading leads to injuries.
Wearables can help in this regard, by keeping track of and recording every single step taken, or move made, or turn or twist and promptly send back a report stating exactly where the workers pose a possibility for injury due to poor movements.
How Wearables can Help Improve Workplace Safety
Wearable technology has become so sophisticated these days that they can accurately measure human movements and postures like never before. Thus they are capable of providing companies with prompt, objective data that can be easily interpreted and turned into effective results.
Wearable technology makes use of certain small sensors that can be placed on the workers, as they go about their daily work routines. These sensors are capable of providing live data regarding their movements, which can be accompanied with high-definition videos that can help accurately single out the risk areas easily. Repeated problematic movements can be identified as a possibility of injury. Alternatively, if the worker hasn’t made any movement for a particular amount of time, the system can automatically trigger an alert to co-workers, to act on instantly.
For example, VINCI, a global construction company in the UK, actually implemented wearables in their workplace. They placed sensors on their brick-laying workers to collect real-time objective data, which resulted in lesser risks of lower back injury and even increased productivity and efficiency. Some of the detailed results were:
- Upto 85% reduction in time spent doing work involving a more than 20 degrees back bending
- An 84% reduction in lower back muscle activation
- A 17% increase in productivity, in terms of bricks per minute
- A 70% reduction in repetitive higher risk associated movements
GPS in Wearable to Ensure Technician and Client Safety
Tracking and monitoring technologies integrated to wearables ensure remote technicians remain safe. ReachOut, for example, helps integrate a right mix of mobile devices and wearable technology with location tracking capabilities. This provides a comprehensive in-the-field safety for technicians and allows clients to tackle tricky “lone worker” problems, no matter how remote the technician’s location.
To support the above facts, the Institute of Management Studies at Goldsmiths, University of London has found that the productivity of people using wearables has increased by 8.5%
There are many more cases where wearable technologies can be used to improve workplace safety. For example, several Australian engineers have developed certain “patches” that are programmed to detect toxic gases and UV radiation, which can immensely help workers in the chemical manufacturing industry.
Another instance is in Rio Tinto, where their coal mine truck drivers use a certain device that resembles a baseball hat, to measure brainwaves in order to keep a check on and avoid fatigue-related problems.
Thus, it is evident that wearable technologies can do more than just reduce work injuries.
On a technical note, aside from the fact that work injuries affect productivity and efficiency, unsafe work environments can also increase the insurance costs incurred by a company. Moreover, hazardous environments, without possible safety precautions, can affect employee morale in a huge way, and in turn, reduce employee retention rates.
Hence, it is in the best interest of every organization to invest in improving the safety of workers, and reducing the risks of injuries. Wearables are capable of providing this much-needed safety, by carefully monitoring and comprehending human movements as well as other environmental factors, thereby helping to maintain an optimum level of health for them and the overall business.
Stay up to date on what's new

Featured Blogs
Stay up to date on
what's new



Talk To Our Experts
The field service industry, as we all know, is at the peak of its transformative stage now. The technological advancements in the industry have been coming on, one after the other for the past few years, and now the rate of the revolution has reached an all time high.
As new tools and technologies continue to take over the field service market, let’s take a look at some of the major trends for the year 2016 and beyond.
- Predictive Maintenance – Last year, we saw the expansion of the Internet of Things as well as a more widespread use of analytics tools to handle all the big data. From this year on, it is time to put those tools to real use, and enhance the predictive capabilities of all connected devices. That way, a more predictive or proactive approach to service can be taken up, along with automation. For example, sensors could be fixed on equipments, and devices, that can notify its users when it needs a repair or when it is due for its regular maintenance. Thus, the whole process becomes automated, as it provides enough insight to the service providers to serve customers, without having them make a service request or call.
 The Internet of Everything – The Internet of Things isn’t exactly a new trend to look out for in 2016, but we will definitely see an increase in its adoption by businesses in various industries, making it sort of an established industry best practice. According to Gartner, there are going to be about 26 billion devices, apart from smartphones, tablets, and computer systems, that are connected through the Internet of Things by 2020. Hence, the range of devices through which people are connected is getting bigger, which is exactly what the field service industry needs. The field service technicians need to be connected with the main office, with their colleagues, with the equipments used in the fields, as well as with their customers in real time. Information captured in the fields, with the help of such intelligent connected devices can then be used further, in predictive maintenance practices too.
The Internet of Everything – The Internet of Things isn’t exactly a new trend to look out for in 2016, but we will definitely see an increase in its adoption by businesses in various industries, making it sort of an established industry best practice. According to Gartner, there are going to be about 26 billion devices, apart from smartphones, tablets, and computer systems, that are connected through the Internet of Things by 2020. Hence, the range of devices through which people are connected is getting bigger, which is exactly what the field service industry needs. The field service technicians need to be connected with the main office, with their colleagues, with the equipments used in the fields, as well as with their customers in real time. Information captured in the fields, with the help of such intelligent connected devices can then be used further, in predictive maintenance practices too.
- Better Integration – As an implication of the “Internet of Everything” phenomenon, there is going to be an exponential increase in productivity and efficiency over the next few years. As mobile devices, equipments, telematics, and the offices are connected and integrated with field service solutions, there can be more chances or opportunities to work closely and communicate more effectively. A custom field service software will be the right way to go about it.
With the help of vehicle tracking, scheduling and routing facilities on mobile devices, field service technicians can take decisions in real-time remotely. It also helps them avoid issues related to reckless driving, control maintenance costs etc., all from a handheld device. All this besides the regular utilities like access to customer history and billing information, location information of colleagues and the like.
- Mobility all the way – We will see most field service companies embracing mobility in the years to come. Field service solutions will take different mobile forms like tablets and smartphones, customized to suit the different business models of companies. Here are some of Gartner’s predictions for 2016 and beyond:
– About 40% of the field service workforce will be mobile
– More than 65% of the mobile workforce will have a smartphone
– Field service organizations will buy up to 53 million tablets in 2016
- A Single Provider – Along with modernization and further technological developments in the industry comes an increasing trend of relying on a single provider for all the functionalities required for work. Most companies entrust a single company to deliver the software and skills to manage their work, employees, and assets. This calls for comprehensive, robust as well as flexible platforms supported by strong providers.
What other trends do you think can be added to this list? Share with us in the comments below. Let’s discuss.
Stay up to date on what's new

Featured Blogs
Stay up to date on
what's new



Talk To Our Experts
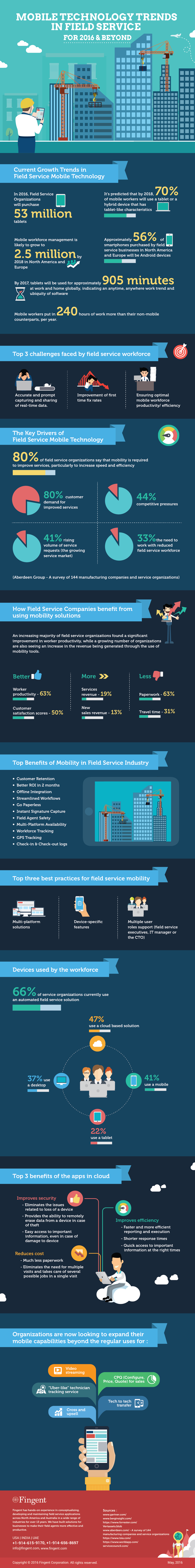
Field service businesses are trying to capitalize on the advantages offered by today’s technologies. Mobile technology, being the most significant among them, has taken the industry by storm, offering increased productivity gains, streamlines work processes, improved field agent communications, increased first-time fix rate, shortened billing cycles, reduced overhead of paper-based field service management and so on. The infographic puts together some recent trends, impacts and state of mobile technology in Field Service Businesses.
Interested in learning more on enabling your field team with mobile technologies? We’d love to know your business requirements and help accordingly, contact our specialist team now.
Share this Infographic On Your Site
Stay up to date on what's new

Featured Blogs
Stay up to date on
what's new



Talk To Our Experts
By now, we all know that we are living in the midst of billions of devices and machines that are connected to the internet and to each other. Need more evidence to believe it?
Well, Gartner predicts the number of internet connected devices and things to grow to almost 21 billion by 2020. IoT is in fact, huge and growing.
We humans are literally on the verge of being outnumbered by connected devices in the coming years. Now, I bet we didn’t see this coming when we first started using smartphones!
And get this, each of these devices, whether they are smart or wicked smart or even not so smart, are constantly collecting data through various sensors around them. In fact, a lot of our personal information is being accessed by our smartphones alone for crying out loud!
Is it almost time to start fearing the appalling situation of “Technological Singularity”?
Are we all going to get phased out by the intelligent machines one day?
We will have to let time answer that question, although we do have a hold over it through security measures.
Security and privacy are two of the most questionable aspects of IoT. Especially, now that the number of devices, as well as the amount of data are increasing rapidly, it becomes all the more difficult to monitor its use.
Connected everything – is it a boon or a bane?
When you take consumer devices like smartphones, think of the data it collects from your applications. It takes note of everything we do with our phones, wherever we go, including things like what we eat, what mode of travel we use, which route we choose, who we communicate with, what pictures we take and so on.
When it comes to fitness and health care, we have wearables and other smart devices that monitor our heart rate, our sleep time, our exercise routines and the like.
Likewise, we have sensors sending and receiving information on a number of devices we use on a daily basis. Combining all this information, along with analytics in the cloud, the value and amount of information that can be collected about our health and lifestyle is massive. The issue here is that, the level of technology has grown so much that, it surpasses the ability of law to control and protect how this data might be used. And needless to say, the endless number of devices being used, the amount of data generated and the applications that use the data, together make it worse. It is pretty hard to ensure security on such a wide scale.
Wearables

Delving a little deeper into wearables, a study in 2015 showed that around 41,000 patents were granted from 2010 to 2015 for wearable technologies. This only shows the pace at which wearables are advancing.They are seen more as a means to overcome some of the common issues of the modern society, and encourage people to move more. They help us in leading healthier lifestyles by tracking our sleep patterns, monitoring temperature, heart rate, glucose levels and the like.
For example, the Microsoft Band, makes use of galvanic skin response sensors, just like the ones used in lie detectors to track your activity levels, heart rate and more.
CES (Consumer Electronics Show) this year saw the first ever Bluetooth connected pregnancy test along with its app.
What we earlier thought to be science fiction, is a reality now.
In healthcare, though, we do have the HIPAA (Health Insurance Portability and Accountability Act of 1996) rules and regulations to monitor and control the sharing of health information. They are pretty strict as well. Devices like Fitbit are majorly being discussed around the world, on whether or not they violate the HIPAA rules. So, we do seem to have a certain safety element around health wearables.
Privacy?
According to a paper published by the Federal Trade Commission (FTC) on Consumer Data Privacy and the IoT, out of many issues that could affect data privacy, there are four basic ones that need our constant attention, namely security, data minimization, choice, and notice.
Data minimization is the practice of limiting the amount of data collected from various devices, to only what’s necessary for the application, and deleting any old information as well, all for privacy purposes. The paper mentioned that such data minimization affected innovation, as even though collecting extra information may not seem to be useful at present, it may help future applications and functions, and restricting such possibilities affects the chances of better, improved applications for the consumers.
Notice and choice refer to the information given to the consumers about the amount and kind of data they are going to be sharing, and the option for them to opt in and opt out.
How many times have you seen an application asking for access to your smart phone’s camera, contacts, location and the like?
Even an app that doesn’t seemingly need to read your contacts, like a fitness app, prompts you for such information. Sometimes these permissions are hidden in clickthrough approvals of end user agreements necessary for the app to function or to activate a device or an app.
And many other apps claim to use “bank grade security” and “encryption” as protection measures for your data, but seldom do people know even the meaning of those terms.
Hence, the bottom line remains, that security and privacy are indeed two important aspects of IoT and data collection. But a lack of standards, and rules to ensure adherence to the same makes it an ever growing concern in the IoT era.
What are your thoughts on security and sharing of data across devices? Let us know in the comments below.
Stay up to date on what's new

Featured Blogs
Stay up to date on
what's new