Considering the recent surge of cyber-attacks, securing a newly built software application is of the utmost importance, now more than ever!

“The hacker didn't succeed through sophistication. Rather he poked at obvious places, trying to enter through unlock doors. Persistence, not wizardry, let him through.”
– Clifford Stoll, the system administrator who helped with the capture of hacker Markus Hess.
The key is to secure each and every door making it hackproof. In today’s digital world, secure software helps protect sensitive user information from theft or manipulation, prevents financial and legal consequences, maintains trust in the product, and safeguards the reputation and brand of the company.
Though there have been many more companies adopting secure software development, there are still many who skirt danger.
0
%
Did you know ?
60% businesses have had production applications exploited by OWASP top-10 6040R vulnerabilities over a period of just 12 months.
– Enterprise Strategy Group
You don’t want to be one of them, do you? So, let’s take a deep dive into what you will need to ensure watertight security.
What Is Secure Software Development?
Secure software development essentially is the process of designing, building, and testing software to minimize the risk of security vulnerabilities. It involves incorporating security considerations throughout the development life cycle, from the initial design phase to the final deployment of the product.
With the assistance of Secure Software Development Practices, developers can curate better and safer software applications. A poorly constructed application is subjected to a high risk of attackers who can compromise information and resources, and harm other aspects of the company. It is always smart to start applying good security protocols as part of the security architecture well before the development process when requirements are formed.
What is a Secure Software Development Policy?
The Secure Software Development Policy is a document that houses a set of guidelines of good practices that analysts and software developers must adopt to make the process of designing systems more reliable, balanced, stable, and protected against threats. It elucidates the roles and responsibilities of stakeholders, outlines security measures, and provides guidance on incident management and response.
The first technical step in a secure software development policy is to form the governing rules for programming languages and coding. Programming and coding languages contain numerous weak spots, so analysts and developers must be well-informed on the strategies that efficiently minimize attack routes.

5 Software Security Goals
Aside from eradicating threats, correctly implemented software security can evidently provide significant business benefits. While designing secure software, developers have to remember to keep the application security code basic and ensure that security behavior is simple to further extend in the future.
5 major goals of software security are:
#1Applications Use Modern Security Standards
Using Modern Standards or security is the most important aspect to consider while developing secure software. Each standard should be carefully appraised by professionals in order to stunt threats and mitigations.
Selecting a well-reputed Identification and Access Management (IMA) is the right decision since this will directly impact your business outcome. Making the right technical investments and selecting the right partner is very important.
#2A Secure Token Design That Protects APIs
Most developers and analysts clearly understand that an application will redirect to the IAM system when user authentication is needed. Following this, the application calls Application Programming Interface (API) using tokens. The IAM system then writes secure values into the tokens titled as “claims”.
These tokens are identified by your APIs later to trust and use for authorization. For example, user ID, email, tenant ID, role, or subscription levels are encoded into tokens. IMA is tasked with having to retrieve stored business data while internet clients receive only confidential reference tokens.
#3Users Authenticate In Many Ways, With A Single Identity
Your applications are enabled to run a simple code flow which is enabled by your IAM system, after which many ways of user authentication can be built. Durable authentication also requires a data integrity design.
Every business data usually has its own user concept, with business user IDs stored beside business resources. The developed system should be able to avoid duplication of users with respect to identity or business data when users apply different authentication methods.
#4Engineering Teams Follow Security Best Practices
Creating secure software developments usually has a complex framework and applying it can be highly architectural. It is astonishing how frequently expensive mistakes are made while developing secure software.
These mishaps can delay time to market or affect future productivity and be a burden on your business’s finances. Considering that most analysts and developers are not security experts, they should always access detailed IAM online resources.
#5DevOps Teams Operate Production Systems Securely and Reliably
Your company IAM provider should provide a support package along with punctual access to real product experts. During production, the DevOps team operates the company’s APIs, the API gateway, and the IAM system.
These components are programmed to interact frequently. Hence it is beneficial if they are placed next to each other inside your backend cluster. What works best here is a cloud-native approach. It also enables teams to restrict endpoints that are exposed to the internet.
What Is a Secure Software Development Framework?
A Secure Software Development Framework is a set of fundamental, sound practices for secure software development. It is a comprehensive approach to building software that integrates security considerations throughout development. It includes guidelines, consistency, standards, best practices for designing, building, and testing secure software, and processes for incident management and ongoing maintenance and updates.
What Is a Secure Software Development Lifecycle?
The Secure Software Development Lifecycle, also known as SDLC, is a structured procedure that enables good quality software application development, in the shortest possible time with the lowest expense. Among many other functions, secure SDLC ensures that security requirements are gathered alongside functional requirements, routine risk analysis is being undertaken during the design phase, and security testing happens in parallel with development.
There are 5 essential phases of the Secure Software Development Lifecycle –
1. Requirements Planning
Proper planning is always an important aspect of any project development. If your plan is ironclad, then your development process is already 80% foolproof. During this phase, you will have to identify your project’s security requirements. This gives you an essential threshold understanding of how you need to design security protections for the software you’re developing and what aspects of it need more attention.

2. Design
After the completion of the Planning Phase comes the Design Phase. Here the key point to remember is that the software design should be according to the previously conducted planning and should be done keeping the future deployment of the project into the real world in mind.
In this phase, developers implement and code security requirements in accordance with secure coding standards. They should give extensive thought to designing appropriate security architectures, implementing all relevant security requirements and control for a variety of factors, including risk management and legal restrictions.

3. Development
The next phase is the actual development of the software, meaning the actual coding and programming of the application. Here developers must use secure coding standards, they must appropriately implement secure design patterns and frameworks and finally, the development created must take advantage of the latest secure coding practices.

4. Testing
Once the design and development phases are successfully completed, the product can be sent out for alpha and beta testing. Most companies underestimate the importance of this phase and try to skip past it but usually end up regretting their neglect later. Do not be like them. Pass the project through a series of rigorous security tests and hire professional penetration testers to try hacking the software. These testers will record your project’s weak spots and subsequently report them to you. They can also make suggestions concerning the types of improvements you can implement in order to protect your program better.

5. Deployment and Maintenance
The last step of your software development is its deployment, if you have meticulously followed all the above steps then this will be a smooth process. A developer’s work does not end with the deployment phase, however. Developers need to regularly update the deployed applications and address any issues that may arise. Aftercare and maintenance are just as important as any other step of secure software development.

What Happens Without Secure Software Development?
The internet has a large supply of hackers who are waiting for easy opportunities to sabotage software applications through hacking, phishing, and ransomware attacks. These hackers identify specific flaws in the software’s security barriers and exploit them to interfere with the software’s system. This later leads to theft of confidential information, financial loss, and damage to a company’s reputation and brand. The only way to prevent this from happening is with secure software development. Software defects and vulnerabilities can lead to legal consequences and compliance issues, resulting in costly penalties and fines.
Four Stages To Organize a Secure Software Development Processes
Ensuring security needs to be a well-thought-out and carefully implemented process. This process is sometimes underemphasized in organizations, Take for example, the training that developers receive in this regard.
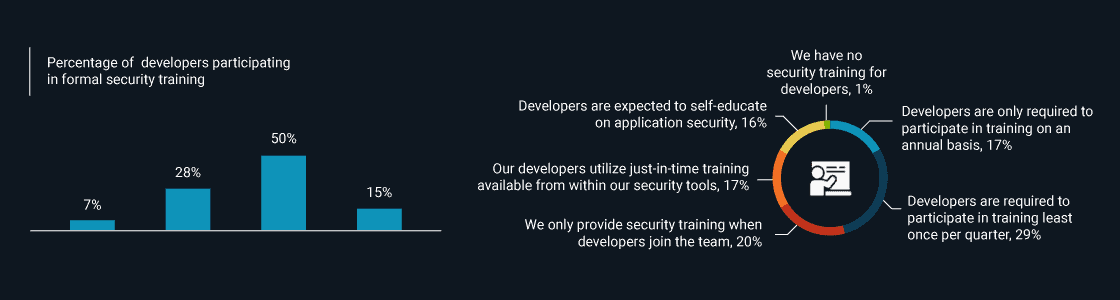
– Enterprise Strategy Group
Things like this can derail your plans to ensure the best security for your business. This is why, we have compiled a list of steps that you need to take to organize a secure software development process.
Prepare the Organization:
This stage is simply about clearly identifying both internal (e.g., Policies, risk management strategies) and external (e.g., Laws, regulations) development security requirements.
Practice
Secure Software Development Framework roles are distributed and teams begin preparing with role-specific training. Supporting tools are also implemented to improve speed and efficiency and security checks are instated.
Tasks
This includes defining, communicating, and maintaining all security requirements. Ensuring that training schemes are prepared, management support is attached, and tools are appointed us vital. Finally, benchmarks are defined to register the achievement of security standards.
Examples
- Defining specifics (coding practices and architecture requirements),
- Reviewing and updating security requirements
- Assigning SSDF-related roles training plans
- Specifying tools and incorporating automation
- Creating proof and evidence of secure development-related actions
- Recognizing key performance indicators and reviewing all security check evidence
Protect the Software:
This stage comprises protecting the code and ensuring that the software’s integrity is safeguarded.
Practice
It focuses on protecting code from unauthorized tampering, validating the software’s integrity, and shielding the software after deployment.
Tasks
Its task is to store codes based on the least-privilege principle to ensure only authorized users can access it. Consequently, a copy of every release with listed components and verification information is proffered to every customer.
Examples
- Store code in safe, restricted-access depositories
- Track all code changes
- Using cryptographic hashes for deployed applications and permitting only trusted certificate authorities for code signing
Produce Well-secured Software:
This stage includes multiple steps and involves numerous actors and practices.
Practice
- The software is fabricated and reviewed to line up with security requirements.
- Third parties are thoroughly examined for compliance.
- Developers write code, configure the build process, and automated means to uncover vulnerabilities.
- The software is designed with secure default settings for protection and trusted components are often reused in production.
Tasks
These include creating a loyal component list, assessing risk, studying external security requirements, and communicating standards to third parties while simultaneously examining their compliance, and verifying code from multiple angles through review. Final tasks also include designing and performing alpha and beta tests, documenting the results, and fixing all uncovered issues.
Examples
- Study weak-spots reports on previous releases to ensure all potential risks and security requirements are tackled
- Include security requirements in third-party contracts
- Avoid all unsafe building functions and only develop in spaces that mandate safe coding
- Employ a combination of reviews, dynamic/static report testing, and penetration testing to detect software shortcomings
- Create an organized depository of trusted building components
Respond to Vulnerabilities:
Hunting for vulnerabilities is the biggest part of a security professional’s job. This final stage focuses on rectifying existing vulnerabilities and collecting data for future prevention.
Practice
Once the vulnerability is identified and confirmed, it must be pragmatically prioritized and mended. Speed is essential in decreasing the time that threat hackers have to launch attacks. In addition, once mitigated, it is always beneficial to analyze the shortcoming’s root cause to help prevent future mishaps.
Tasks
They include collecting customer information and diligently testing code for any undetected flaws, creating a team to plan, processing rapid vulnerability responses, creating and implementing a rectification plan for each discovered malfunction, and determining the causes in order to construct a well-informed knowledge base for the future.
Examples
- Create a vulnerability report and response program
- Employ automation to effectively monitor malfunction data and automated code analysis
- Gauge the resources required to fix each mishap while prioritizing correction
- Identify and document the root causes of malfunctions automatic future detection and implement accurate adjustments to the Secure Software Development Framework.
Examples of Software Development Security Efforts
Software security efforts mainly focus on security testing at each developmental stage, from the design and development to the deployment and maintenance. These efforts also include applications designing to ensure that your software is fool-proof, implementing secure coding practices, running regular security testing and audits, incorporating security risk factors, and following industry-standard security frameworks such as The Open Web Application Security Project (OWASP) and National Institute of Standards and Technology (NIST).
Top 10 Software Security Development Best Practices
The threat of software vulnerability is very real. Consider this report from Qualys Web Application Scanner. The report includes findings after scanning 370,000 web applications. The scans revealed more than 25 million vulnerabilities!
Plugging these vulnerabilities is of utmost importance, so let’s get cracking on how this can be achieved through these 10 software security development best practices
It is a great benefit to implement a Secure Software Development Life Cycle (SSDLC) approach to your software development process in order to decrease cyber-attacks and threats. The SSDLC approach is not only restricted to developers and the security team this way no one without authorization can access it. It can also be easily endorsed by other organizational teams to enhance security over multiple stages of software development.
Technologies use multi-factor authentication such as One Time Passwords (OTP), Certificate Based Authentication (CBA), and Context-Based Authentication. All of these methods proffer flexibility and yet keep the security door shut air-tight. It is absolutely important to be aware of who accesses the software and why they do so, ignorance here will cost you heftily in the long run.
“Quantum Encryption is essential to protect our digital assets and infrastructure from attackers”, as quoted by the president and CEO of Coleman Research, Kevin Coleman is right on point. Encryption means to protect data from being stolen, misused, or compromised by packing data into a secret code and programming it such that a unique digital key can unlock it. Encryption through transit and at rest is the only way to properly secure the confidentiality of user data on a network.
As we discussed earlier, security tests are an intrinsic step in software development. They effectively help spot weaknesses in the system before they can be ravaged by a cyber attacker, hence reducing the overall risk of a security breach or data theft.
When it comes to technology, consistent upkeeping and mindful maintenance is very important. This implies the need to install “patches” that are released by the software developers to cover any security holes found in their products. Updating your software regularly helps enhance existing features, patch security flaws, implement additional new security features, fix any issues that may have arrived below the surface, and improve overall performance.
An intrusion detection system (IDS) is a famous system that scans network traffic for malicious activities or policy violations and immediately alerts users when it is spotted. All illegal activities or violations are often recorded either using a central Security information and event management (SIEM) system or notifications sent to the administration. Any dangerous activity even from insiders will be recorded and reported by this system.
Everyone should be aware and prepared. Security awareness and training for developers and end-users are important as it protects an organization from cyber attacks which will result in data breaches. The center focus of this training is to prevent any incidents that could lead to loss of brand reputation and cause financial losses. Effective education and knowledge dissemination will also help your software developers write secure applications from day one. This training should include learning basic information about common software development vulnerabilities and information about how hackers and cybercriminals work.
“Least privilege” is a concept where users trying to access applications are given only the minimum resources and permissions needed to run securely and perform their job. According to PLOP, users are proffered permission to only read, write or execute the files or resources necessary to do their jobs. This way, if there is any vulnerability in the web apps or back-end services, hackers cannot use it as an entry point.
A widely registered risk in software development is faultily written code. The basic crux of any application is its code and if this code is not written well, the entire application will fall apart. Applications with poorly written codes are especially challenging to secure. Good coding practices such as input validation, output encoding, error handling, and secure storage should be strictly followed. Lethargy and ignorance should be avoided as much as possible when it comes to coding.
Finally, develop and test incident response plans to ensure a quick and effective response to security incidents. A strong incident response plan will provide guidance on what to do in the event of a security breach and is vital in ensuring that organizations recover from an attack or other security event spontaneously. Incident response planning outlines how to minimize the damage of security breaches, restore business operations, improve recovery time and reduce negative publicity and avoid high costs for damage control.
How Fingent Can Help
Developing secure software can be a daunting task but with the right support from your partner, it can run smoothly without any hiccups. Trusting the right Software Development Solution with your project is very important and Fingent exemplifies a perfect partner.
Fingent top custom software development company, ensure that your security-related requirements are addressed across the development lifecycle, governance, and hosting. Our solutions are tailor-made for each client and take a cloud-based hosting approach which ensures airtight security. We have successfully completed more than 800 projects and have earned the trust of big companies such as Raymond, Johnson&Johnson, Royal Enfield, Sony, Apollo, and many more. We can do the same for you too. Give us a call and let’s start discussing your security needs.








































